
In today's hyperconnected world, cybersecurity teams are fighting an uphill battle. The modern cyber threat landscape is evolving fast. New tools are flooding the market. Data is spiraling out of control. The result is alert fatigue, burnout, and too many security professionals stuck in the weeds, unable to see the forest for the trees. We built Tonic to fix this reality.
Threat actors are becoming more sophisticated, executing attacks with increasing volume, velocity and ease. They are increasingly using AI to scale their campaigns, compounding the frequency and impact of breaches.
At the same time, the attack surface of companies is constantly expanding. New security tools are flooding the market to address these new threats, generating huge undigestible amounts of data. Tool sprawl is so bad, that according to Gartner, the average organization juggles between 60 and 70 security tools and work with 10 to 15 different vendors.
Clearly, more tools do not mean more clarity. In fact, they often introduce more confusion from loads of data that leave security professionals overwhelmed, struggling to discern what matters to the business. Security teams cannot catch-up as they are buried in endless alerts, vulnerabilities, misconfigurations, and unpatchable weaknesses. Small and medium sized businesses deal with hundreds of thousands of findings daily. Large enterprises face millions!
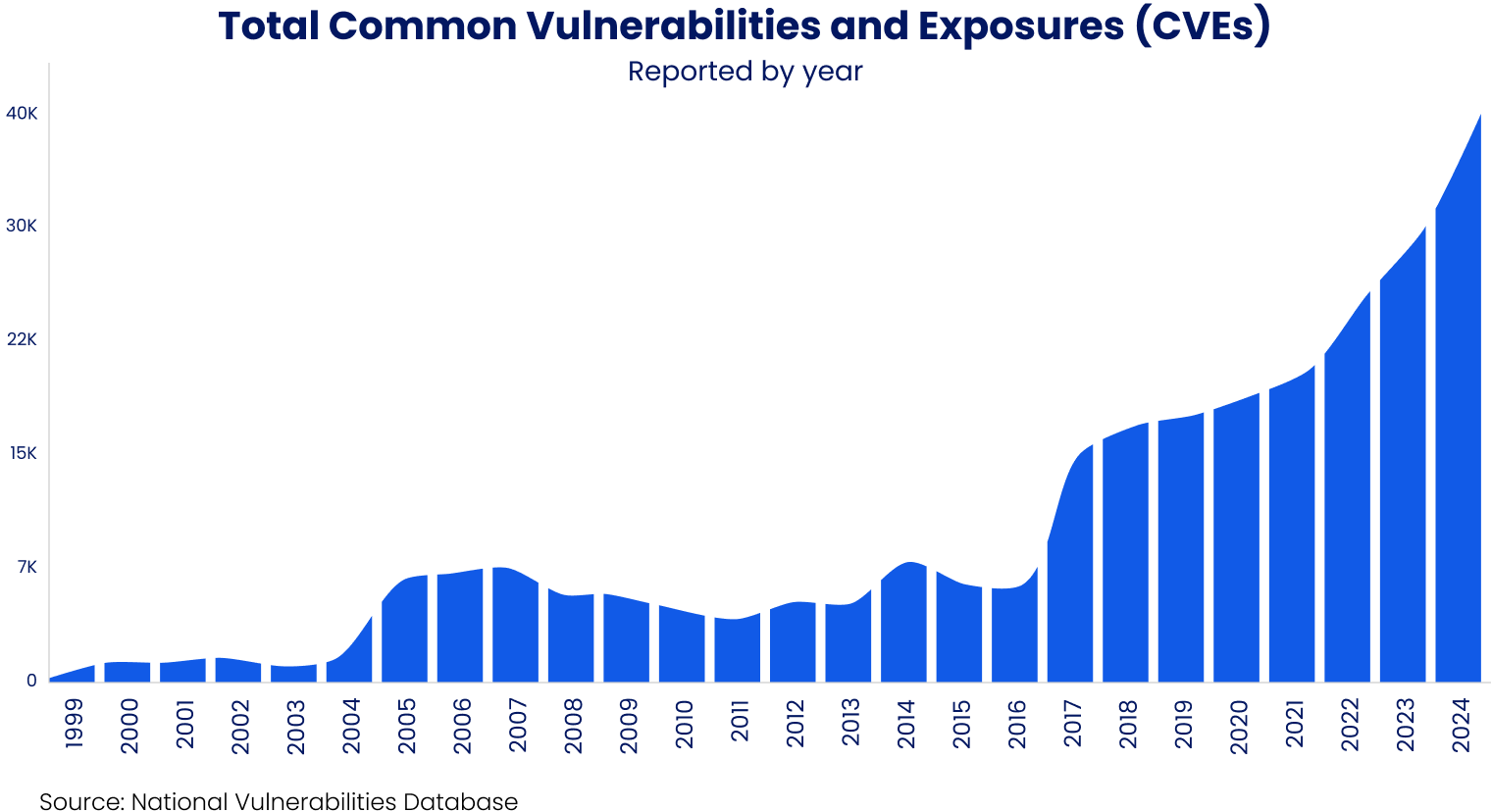
Legacy vulnerability and attack surface management tools aren’t keeping up. They leave too much noise and open ends: a tangled mess of false positives, duplicate findings, context-less data, and minor issues that masquerade as major ones.
Vulnerability Management suffers from significant tech-debt, with catastrophic outcomes:
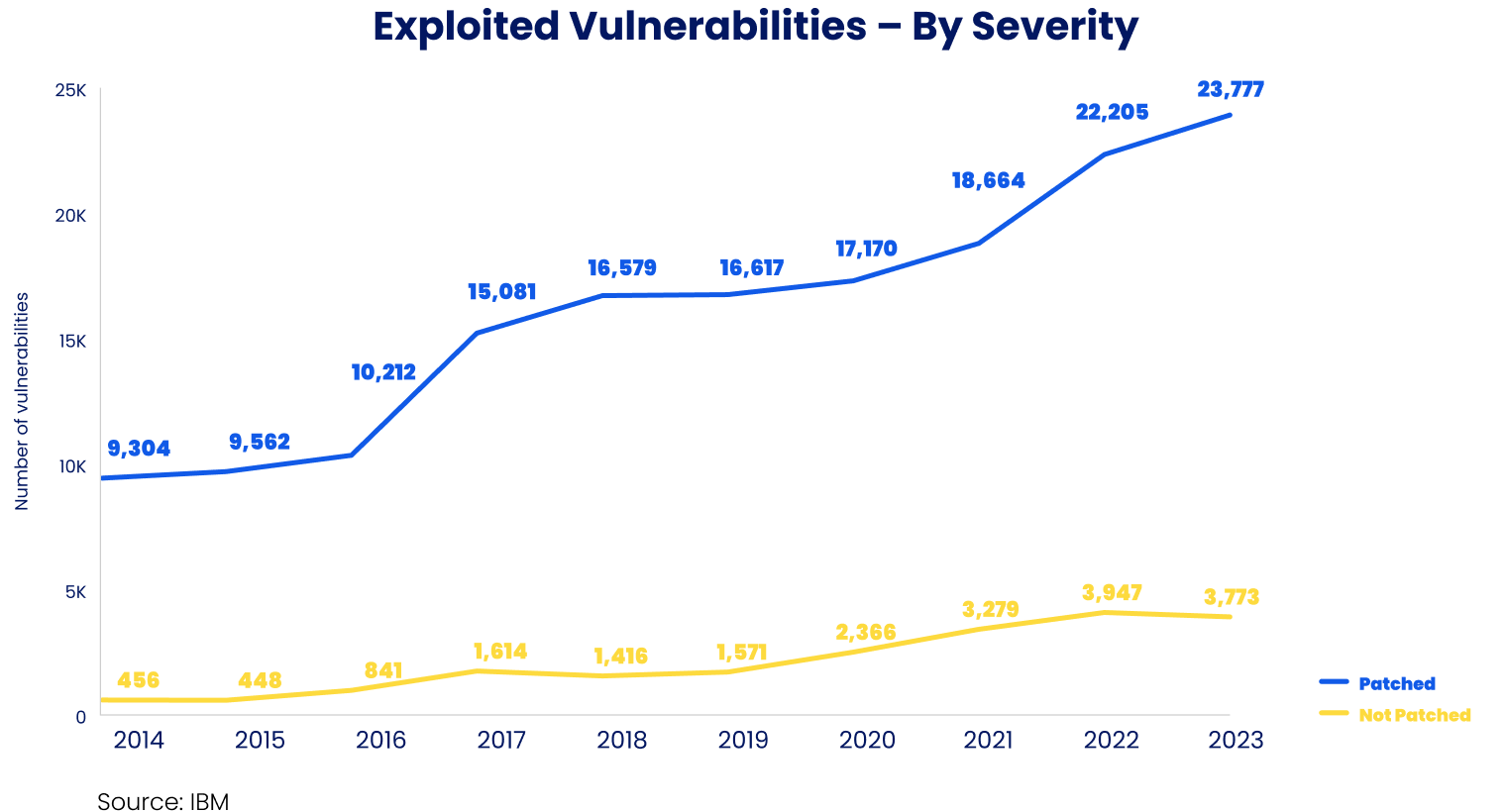
.png)
After many years of doing incident response in cyber and physical domains, I learned firsthand that most incidents are predictable and preventable They don’t just appear in hindsight. We could have actually pre-empted or avoided them using the information and capabilities that we had at our disposal.
The exploitation of preventable exposures continues to rank as one of the top root causes of cyber breaches. Successful preemptive defense or exposure management depends on our ability to read the “writing on the wall” in time: that vulnerability that was mis-prioritized and is now being exploited, or that alert that was not escalated because it was mis-triaged.
Spotting and diffusing these expected harmful surprises hinges on our ability to cut through complexity and noise and prioritize findings in a timely manner.
The real problem is not lack of visibility. It’s lack of context.
Security teams are forced to navigate a complex security landscape without easily attainable context that is meaningful and actionable –especially business context.
This great divide between digital assets and business context highlights something that is fundamentally broken in today’s cyber risk management:
So, what’s broken? None of the tools and controls (preventive, detective, corrective, compensating, you name it…) that are used to treat cyber risk, can effectively connect the dots and trace the risk and the control to the business process that needs to be protected.
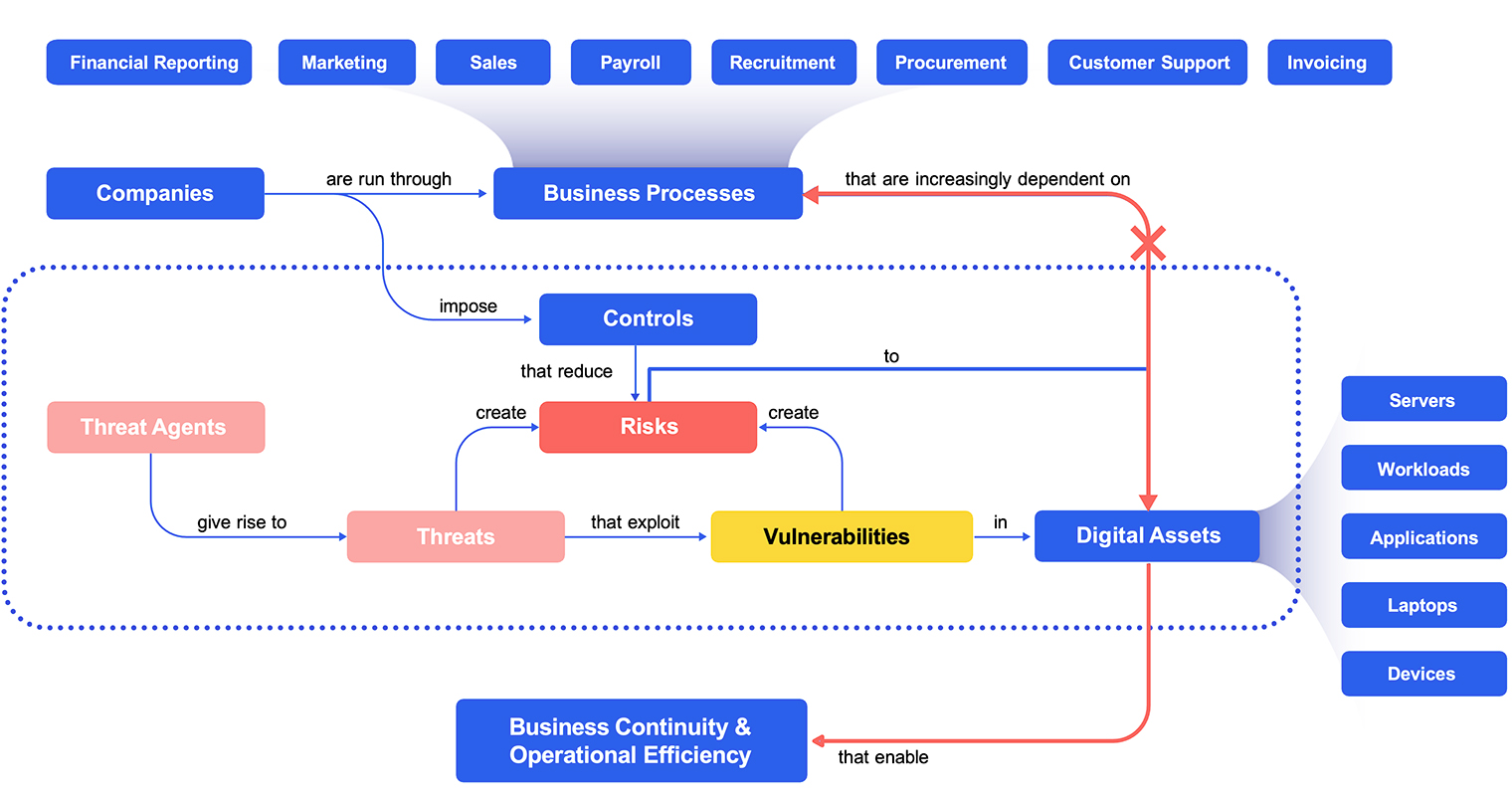
Let’s take an example from vulnerability management.When a vulnerability appears, security teams must be able to quickly understand:
Unfortunately, fetching the context to answer these questions today requires a slow, manual and frustrating process. And the consequences are real:
At Tonic Security, we believe security vendors and tools should make you feel stronger, not more afraid. They should be the calm in the storm, not another layer of confusion. They should super-charge your teams, not slow them down.
We believe context is king! That meaningful and actionable context is crucial for efficient prioritization, timely remediation, and effective risk reduction.
Our mission is to empower security teams with unparalleled visibility, context and focus, so that they can quickly and incisively prioritize and remediate business-critical exposures. Our own domain-specificAI agents and proprietary Data Fabric make this mission possible.
If you’re ready to cut through the noise and strengthen your security posture we invite you to explore how Tonic can help. Contact us.

Sharon has over 25 years of experience in cyber, intelligence, and operations. He began in Israel’s elite military intelligence units, where he served as CISO and CIO of the Home Front Command, and later as COO of the Intelligence Analysis Division. After that, Sharon led biz dev and delivery at Sygnia, a top-tier incident response and cybersecurity consulting firm. During this time, he identified a critical unmet need across the industry. That realization led to the founding of Tonic, which sits right at the intersection of cyber, data, and AI.