- Home
- CTEM Framework


Security leaders are no strangers to vulnerability management. For over two decades, VM has been the frontline mechanism for discovering and fixing potential weaknesses in IT systems. Yet, despite advancements in scanning tools and vulnerability databases, breaches continue to rise. Why? Because the attack surface has exploded beyond what traditional VM can handle.
With the rise of cloud-native architectures, hybrid workforces, SaaS sprawl, and ephemeral infrastructure, organizations now operate in environments that change daily, sometimes hourly. Traditional VM was designed for static environments where monthly or quarterly scanning cycles were enough. That model is obsolete.
Further complicating matters is the overwhelming number of vulnerabilities discovered each year - over 40,000 reported in 2024 alone! But not all vulnerabilities pose equal risk. Most are never exploited. The problem isn’t identifying vulnerabilities; it’s identifying which ones matter and responding in time. This is where vulnerability management breaks down: it generates too much noise, lacks contextual awareness, and struggles to prioritize in line with business risk.
Gartner predicts that by 2026, organizations that prioritize their security investments based on a Continuous Threat Exposure Management (CTEM) program will be three times less likely to experience a breach. It further predicts that by 2028, organizations enriching SOC data with exposure information will halve the frequency and impact of cyberattacks.
Exposure management is not just a rebranding exercise. It represents a necessary and strategic evolution of cybersecurity operations. Rather than focusing solely on identifying software flaws, exposure management broadens scope to cover new areas of the attack surface, encompasses disparate types of findings, and continuously enriches them with multi-dimensional context. It looks at how those flaws intersect with assets, business processes, threat intelligence, and real-world attacker behavior.
.png)
Exposure management asks a different set of questions: Which assets are exposed right now? Are they business critical? Is there an exploit available? Are we seeing activity related to this vulnerability in the wild? Do compensating controls exist? These are the questions that define actual cyber risk.
.png)
This broader, contextual approach requires a shift in tools, processes, and mindset. It also demands better collaboration across the organization. Exposure management is a team sport. Security, infrastructure, DevOps, and business stakeholders must work together to reduce meaningful risk, not just fix issues that scanners surface.
The following table summarizes the main differences between traditional Vulnerabilitity Management and modern Exposure Management:







Gartner’s CTEM framework provides a structured methodology for making exposure management operational. At its core, CTEM is about continuously assessing the exposure level of your digital environment, validating real risk, and ensuring timely remediation. It is not a product - it is a program.
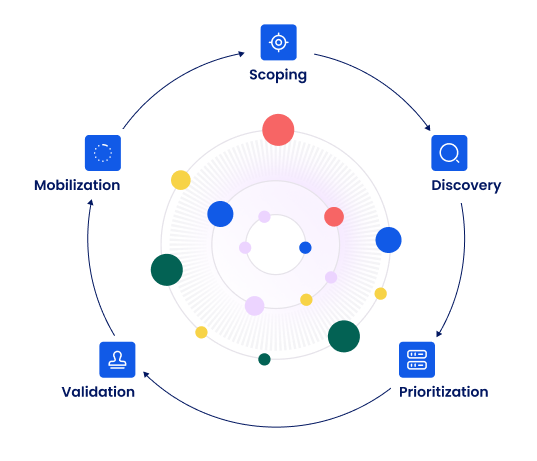
This is the foundation. Organizations must define what they want to protect, what their risk appetite is, and which systems are most critical to operations. Business alignment is essential; without it, prioritization will be misaligned.
You can’t protect what you don’t know. Discovery must include known and unknown assets, cloud workloads, shadow IT, SaaS applications, APIs, and development infrastructure. Tools like CAASM and EASM help build this inventory.
This is where exposure management substantially diverges most from traditional VM. It’s not just about severity - it’s about context. Prioritization includes reachability, threat intelligence, likelihood of exploit, business impact, and resilience, among other factors.
This step is important but often skipped. Use attack simulation, red teaming, or purple teaming to validate whether the exposure is exploitable in your specific environment. Validation turns theory into actionable reality.
Remediation efforts must be tracked, measured, and supported with process ownership. Exceptions must be managed, timelines enforced, and workflows automated. This phase ensures exposures are actually closed and risk is reduced.
The following table summarizes the key characteristics of the five phases of CTEM:





Tonic accelerates prioritization and remediation of vulnerabilities and threats with a Context-Driven Unified Exposure Management platform. Powered by Agentic AI and a security Data Fabric, Tonic extracts meaningful and actionable context from unstructured organizational knowledge and threat intelligence, empowering security teams with superior visibility, dramatic reduction in false positives, and a sharp focus on findings that matter. Leading organizations, including Fortune 500 companies, rely on Tonic to slash remediation time and reduce risk to key business processes.

