
For years, organizations have invested heavily in cybersecurity strategies, regulatory compliance efforts, and governance frameworks. Yet many CISOs still face the same uncomfortable question from boards:
“Are we actually reducing risk?”
The truth is that most companies struggle not because they lack a strategy, but because they lack a way to operationalize it. Sometimes it feels like strategy and risk live on Mars, while security operations live in Venus. The result is not surprising: misaligned priorities, inefficient remediation, and a false sense of security.
One of the biggest breakdowns in organizations today is the disconnect between how business leaders think about risk and how security teams describe it:
This misalignment is often mirrored within the security team between:
Here’s an example:
The GRC team flags “payments availability” as a top 3 enterprise risk. Meanwhile, SOC and VM teams are drowning in critical CVEs on lab systems and legacy file servers. Without a shared map connecting business services → assets → exposures, no one can show how today’s backlog reduces the payments risk, or whether it affects it at all.
This is how well-intentioned teams accidentally work against each other.
Context-aware exposure management can act as the connective tissue that unites these two worlds. Instead of producing raw lists of 2findings, it shows:
When security leaders present risks in terms of business impact - downtime risk, financial exposure, regulatory implications - stakeholders finally understand why certain issues deserve attention. This shared language goes a long way in helping CISOs portray cybersecurity as a business enabler, rather than just a cost center.
Organizations that bridge this gap focus on shared governance:
With shared governance in place, the business sets the direction, and security operations execute it with precision.
Traditional risk assessments — quarterly reviews, annual audits, periodic scans — were built for a slower world. Today, assets spin up and down daily, business apps deploy weekly, and attackers exploit exposures within hours. Periodic assessments don’t just lag; they create blind spots. And blind spots are where attackers thrive.
To keep up, organizations are shifting to continuous, automated, integrated assessment, built on the core pillars of a Continuous Threat Exposure Management (CTEM) cycle:
Scope → Discover → Prioritize → Validate → Mobilize
A continuous model offers advantages snapshots cannot:
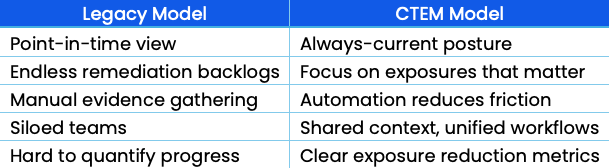
With this shift, security posture becomes accurate, timely situational awareness, not outdated documentation.
One lesson from modern incident response is clear: context breaks silos.
Different teams historically used different tools - scanner dashboards, SIEM alerts, risk registers - none of which talk to each other. Exposure management creates a unified operational fabric:
Context is by nature “boom agnostic”, equally valuable before and during an incident.
Before an Incident (left of boom): A unified context graph, such as Tonic’s business blast radius, can show:
This helps teams proactively harden the environment based on business impact and exploitation likelihood.
During an Incident (right of boom): The same context graph can now tell responders:
One graph. Two modes. Continuous business-informed security.
For years, security teams have been conditioned to prioritize remediation based on technical severity. But attackers do not care about CVSS scores. They care about opportunity, access, and business impact.
This is precisely where many cyber risk strategies break down inexecution: technical scoring replaces business risk logic, and teams are left chasing noise instead of reducing real exposure.
To operationalize cyber risk strategy, organizations need to shift to context-driven prioritization, ranking issues based on factors such as:
Here are some examples:
In a traditional model, these may be buried under CVSS-critical items on low-value assets. In an exposure-context-centric model, all three rise to the top because they matter most to the business.
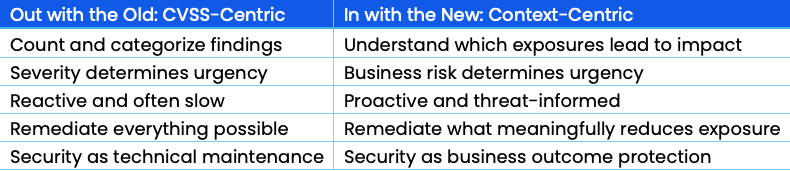
Prioritization is where strategy becomes execution. It is the battlefield where organizations win or fail.
In spite - and because - of advances in technology, many teams remain stuck in reaction mode, overwhelmed by noise and forced into firefighting. This is neither natural nor sustainable.
Defenders should not be scrambling to keep up. They should set the tempo. But the best defense can’t be offense - it should be anticipation, preparation, and preemption.
When risk strategy is aligned with operations, defenders stop chasing what adversaries did and start preventing what they could do next. This requires a shift from a traditional detect → respond model to a prevent & preempt disposition. That’s where context-driven exposure management begins to move the pendulum back to where it belongs, helping teams:
Here is a battle-proven best-practice framework you can adopt to bridge the gap and turn cyber strategy into operational efficacy:
Tonic Security’s Unified Exposure Management platform was built to decisively close this gap. With Tonic, security teams can:
Learn how Tonic gives defenders the context and precision they need to protect what matters most. Contact Us.

Sharon has over 25 years of experience in cyber, intelligence, and operations. He began in Israel’s elite military intelligence units, where he served as CISO and CIO of the Home Front Command, and later as COO of the Intelligence Analysis Division. After that, Sharon led biz dev and delivery at Sygnia, a top-tier incident response and cybersecurity consulting firm. During this time, he identified a critical unmet need across the industry. That realization led to the founding of Tonic, which sits right at the intersection of cyber, data, and AI.